
All-Out Anti-Phishing
How To Prevent Phishing Attacks?
What Is Phishing Attack?
Phishing attack is one of the most common "scams" on the internet. Scammers will impersonate others or companies, and then send various cleverly crafted messages, even using threats and enticements, to trick victims into clicking malicious links, downloading suspicious attachments or providing sensitive information unconsciously such as credit card information, identity information, account passwords, etc.
Phishing attacks have always been one of the most common cyber-attacks encountered by the public. Have you ever seen any suspicious messages when reading an email or using a smartphone?
Below are some examples:
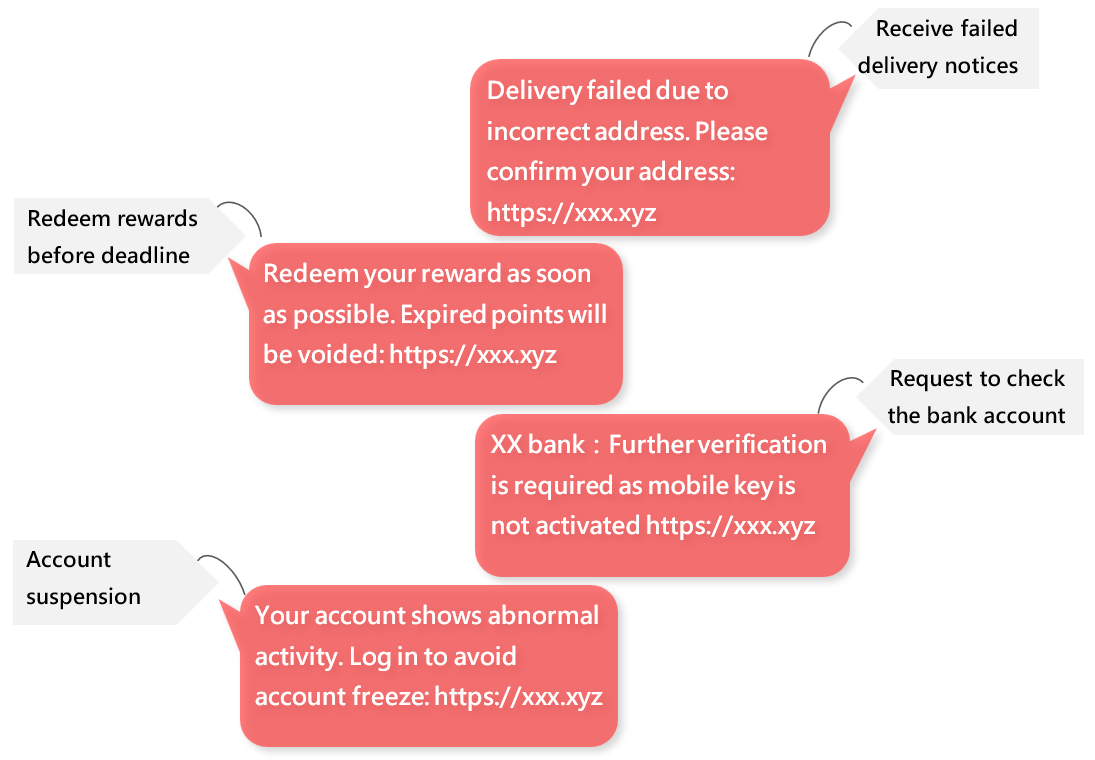
Messages usually have a link that takes you to a fake website that looks similar to a certain organisation's website. Usually, these kinds of fake websites only have one function, which is to ask for personal information such as account passwords or credit card numbers. This is a typical phishing attack!
Among the security incidents handled by HKCERT every year, incidents involving phishing attacks have always been among the top. Scammers know how to create fake messages using hot or juicy topics, and they are also familiar with bypassing security measures. Therefore, new and fake content and websites appear daily.
Why Do Hackers Like To Use Phishing Attacks?
The cost and technical barrier are low, but the benefits are high and are difficult to track.
Templates of fake messages, software for establishing fake websites, tools for generating fake domains, overseas hosting services, and emails or phone numbers of the targeted groups can all be easily found or purchased on the Internet anonymously or with a fake name. After sending a large number of phishing messages, all the hackers need is to wait for the victims to fall into the trap, without the need for direct contact, making it difficult to track.
The Targets
Credit card information, which can be used for transactions;
Account passwords, which can be used to gain access to systems of the organisations to steal confidential information or destroy data;
Personal information such as ID, phone, address, etc., which can be used to impersonate the victim;
Social platform passwords, which can be used to fully control victims’ accounts to post false comments or delete data;
Moreover, many fake websites are hosted overseas. Even if the victim organisation quickly discovers and reports it, the organisation still needs to take time to contact the relevant overseas’ organisations for assistance. Many people have already fallen victim unknowingly. Even the phishing website has been taken down, hackers can launch another phishing campaign easily.
Attack Methods And Channels
Any communication channels can be used for phishing attacks. The following communication methods are some examples:
- Instant messaging such as SMS, WhatsApp, etc.
- Social media platforms
- Online advertising
- QR Code
- Phone
-
Technique
In simple terms, the core of phishing attacks, like deception, is a psychological game. It involves utilizing the weaknesses of humans, luring victims to trust the criminals, and voluntarily handing over sensitive information.
Hackers will find ways to break through and blur our weaknesses in "trust". Since everyone's weaknesses are different, even the same or similar tactics can always have victims who fall for them.
Potential Benefits/Impact Outweigh Suspicion
Hackers falsely claim significant potential benefits/impacts to lower our suspicion: They don't use any special techniques, but put effort into the content, making it closer to people's psychological weaknesses and market environment. The most common method is to impersonate familiar organisations or individuals, imitating their websites, emails, or instant messages to contact us.
Click To ExpandTaking Hong Kong as an example, recent phishing attacks have mainly targeted some well-known loyalty programs, luring victims to click on fake websites in phishing messages by claiming that their rewards are about to expire.
In addition, there has also been an increasing trend of phishing attacks impersonating telecommunications companies recently, which may be due to the impact of the Real-name Registration Programme for Subscriber Identification Module (SIM) Cards.

How to Prevent Phishing Attacks?
There are many security tools available for preventing phishing attacks. As long as we use them properly, we can greatly reduce the risk and impact of phishing attacks.
error
Warning
❌ Common Misconception vs ✔️ Reality
❌ Phishing attacks come from computer systems and they should be more effectively detected by security systems instead of humans.
✔️ Security systems already effectively block most phishing messages, but users still need to handle those that bypass the security measures
❌ Users are not security experts and should not have to take on additional responsibilities for cyber security.
✔️Cyber security is the responsibility of every user. And in fact, you are protecting yourself.
❌ Technology should reduce manual work, users should not have to verify the authenticity of messages manually.
✔️ AI may achieve this goal perfectly in the near future. But for now, users should continue to learn how to verify the authenticity of messages.

How To Detect Phishing Attacks?
In general, phishing messages are often disguised as other organizations or individuals to gain trust and deceive people. However, due to technical limitations, some areas cannot be completely imitated, users can identify suspicious messages by paying attention to details.
Many grammar or spelling errors in content
Misleading or unfamiliar links
Unfamiliar senders or suspicious email addresses
Using urgent or intimidating headlines
error
Hint
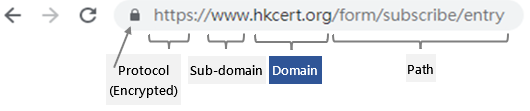
What is a link and domain name?
- A link is an address and shortcut to visit a specific website. It consists of four parts, but only the domain name part is unique and cannot be impersonated.
 Click To Expand
Click To Expand
Handle Messages Carefully
Most people read the title of a message first, and they are easily misled by the "juicy" content, which leads them to follow the sender's instructions and ultimately be deceived. However, we suggest that users should:

Check the sender's email address domain
If the sender's email domain is different from the official domain of the organisation they represent, there is a high chance that it is a phishing email. If a public mailbox is used to represent the organisation, users should pay extra attention, as large organisations generally would not do this. If the email is from an unfamiliar organisation, it is best to call the organisation to verify the sender's identity.

Always remember "There's no free lunch"
Don't let excitement, urgency, or panic override your judgment. Remember that in the online world, as in the real world, overly favourable offers don't happen for free.
Conversely, organisations generally do not send notification messages without detailed explanations or in a threatening manner with severe consequences, and then attach a link for customers to click on.

Check the link domain in the content
Misleading links or links that do not match the organisation's name are very likely to lead to phishing websites. The official domain of an organisation cannot be impersonated; hackers can only mislead users by making a fake link similar to the real one. For example, hkcert852.org, hlcert.org, hkcert.xyz, hkcertorg.dyndns.org, etc., are all not our centre’s official domain. Another technique is using look-alike characters or other language alphabets to confuse users, for example, “1” to pretend “l” (a lowercase of “L”), “0” to pretend a letter “o” or “O”, using Cyrillic alphabet “а” to pretend the English alphabet “a”, etc.
error
Warning
What is Cyrillic alphabet?
It is used by various Slavic (e.g. Russia), Turkic, Mongolic, Uralic, Caucasian and Iranic-speaking countries. Below are the examples of Russian Cyrillic alphabet. The highlighted letters look the same as English letters: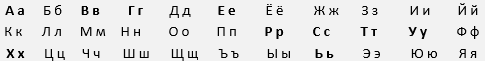
The free search tool " Scameter" launched by "CyberDefender" can identify scams and online traps. It supports checking email addresses, URLs, and IP addresses, and the results will be displayed in different colour warnings.

Check the website you are led to
Double-check the URL domain displayed in the browser for any suspicious elements.
Although the appearance of a phishing website may be identical to the official one, it usually lacks functionality or content, for example, clicking on other pages within the site might result in error messages, or the site contains outdated information. These situations are considered suspicious.
If there is any suspicion, do not open any link or attachment in the message (including those from emails, SMS, WhatsApp, social media posts, etc.) or provide any information to suspicious websites.
Then report the issue to us and delete the related message.
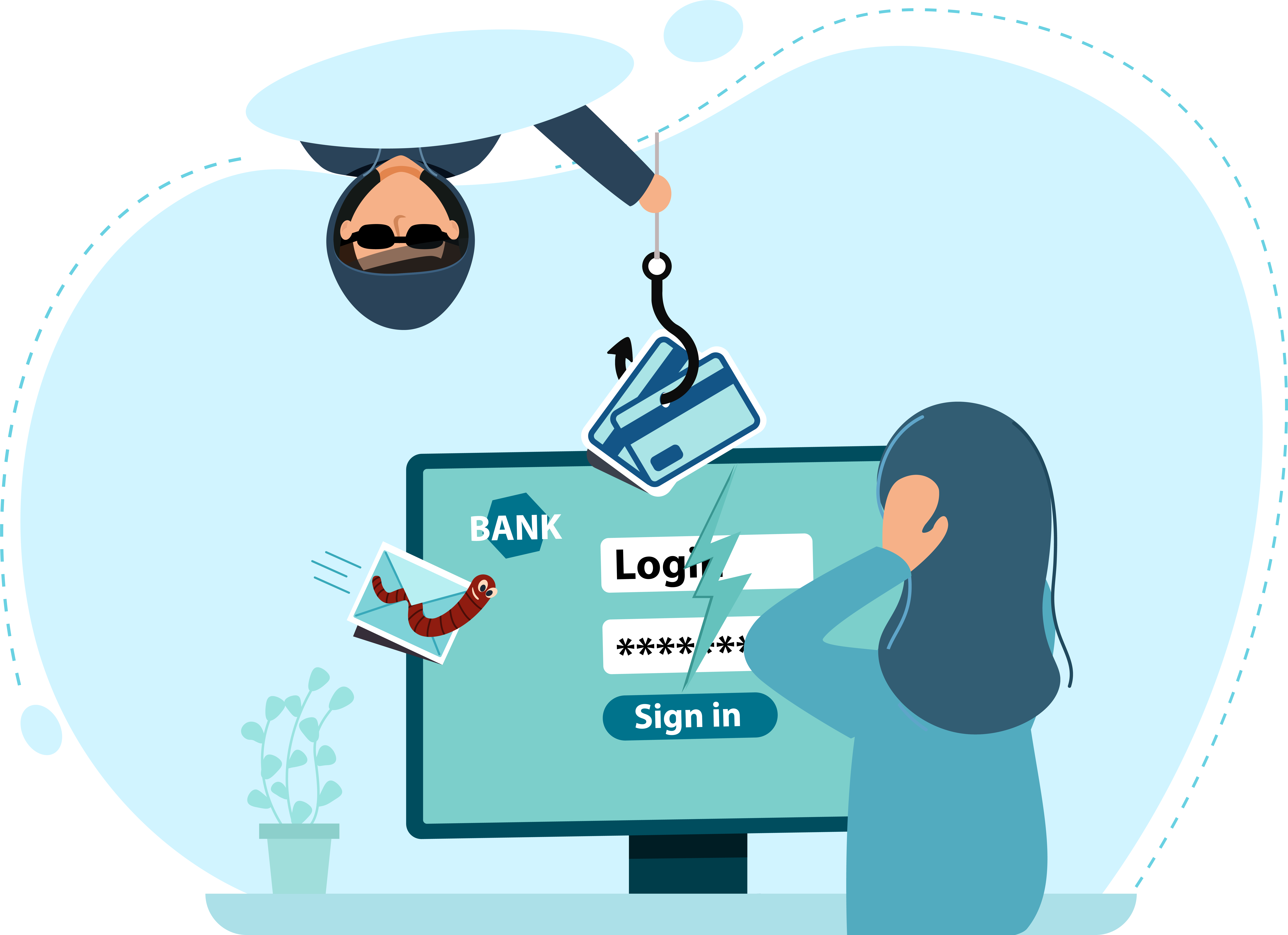
What Can You Do If You Fall Victim?
- Change the passwords for all compromised accounts and contact the relevant service providers to report the incident.
- Set different account passwords for different services.
- Suspend the stolen credit card.
- Closely monitor your accounts for any suspicious transactions or activities.
- Watch out for any suspicious instant messages, impersonating your identity.
- Report to HKCERT.
- Enable two-factor authentication.

Related Knowledge#1
The Importance Of Personal Information
Compared to financial information, such as credit cards and bank accounts, the general public has a lower awareness to personal information protection. This is because we often need to provide personal information in our daily lives, such as opening accounts, registering for promotions, and online shopping. The disclosure of this information seemingly has no consequences.
error
Note
📖The Personal Data (Privacy) Ordinance
According to The Personal Data (Privacy) Ordinance, Personal Data means information which relates to a living individual and can be used to identify that individual. It must also exist in a form in which access to or processing is practicable.
However, this is only because the information you provide is used legitimately by authorized organisations. If the information is obtained by cyber criminals, they can:
- Impersonate your identity to conduct illegal activities
- Hijack accounts to manipulate transactions or steal other information
- Invade personal privacy
Therefore, protecting personal information is extremely important.
Related Knowledge#2
HKMA's Response to Phishing Attacks Targeting Banks
Users' online banking accounts have always been one of the targets for hackers. Hackers impersonate banks to send phishing messages and create fake websites to deceive users into providing login information, then manipulate their online accounts. Often, when users receive messages claiming to be from banks, they tend to become more anxious and less suspicious, making it easier for them to believe the messages are genuine.
Hong Kong Monetary Authority (HKMA) has issued regulatory requirements to banks, requiring banks not to use SMS or email hyperlinks to direct customers to any websites or mobile applications for transactions. Moreover, they are not allowed to request any sensitive personal information (including login passwords and one-time passwords) through hyperlinks.
error
Note
 Messages from Banks
Messages from BanksCheck your bank's SMS messages and other messages in a timely manner and verify your transaction records. Inform your bank immediatelt in case of any suspicious situations, regardless of the amount. Banks will not ask for any sensitive personal information (including passwords) through phone calls or emails.
https://www.hkma.gov.hk/eng/smart-consumers/internet-banking/#using-internet-banking-servicesIn a press release issued in July 2021, HKMA and the Hong Kong Association of Banks once again reminded the public that banks would not use SMS or email hyperlinks to direct customers to websites and apps for transactions or to provide personal information.
error
Note
In accordance with the HKMA’s supervisory requirements, banks will not send SMS or email messages with embedded hyperlinks directing customers to their websites or mobile applications to carry out transactions. Nor will they ask customers to provide sensitive personal information, including login passwords and OTPs, via hyperlinks. So if members of the public receive SMS or email messages with embedded hyperlinks requesting them to input internet banking login credentials, these messages should not originate from banks. The public should think twice before clicking any hyperlinks purportedly sent by banks.
https://www.hkma.gov.hk/eng/news-and-media/press-releases/2021/07/20210706-3/We suggest that if citizens receive messages and links claiming to be from banks, which directly prompt users to conduct transactions or provide personal information, they should verify and report this to the relevant bank.
Citizens can also pay attention to the fraudulent website announcements issued by HKMA and banks to learn more about fake bank websites and avoid losses.
Related Knowledge#3
Phishing Attacks Also Highlight the Issue of Reusing Passwords
With the increasing digitalisation of businesses, we have more and more online accounts. Many platforms use the user's email address and a self-defined password as authentication. Some people use a Password Manager to record account passwords, but some users, to avoid hassle and forgetting passwords, have the bad habit of setting the same password for different accounts.
If a user accidentally falls for a phishing attack and exposes their account and password, hackers can use this stolen login information to attempt to access the user's other accounts, causing cascading losses. If the user also sets the same password for internal company systems, it can even give hackers the opportunity to infiltrate the company, with serious consequences.
We suggest users:
- Do not reuse passwords and change them regularly.
- Keep passwords absolutely confidential; do not share them with anyone and beware of phishing attacks.
- Enable multi-factor authentication to enhance account security.
Phishing Example and Quiz
We compiled some examples of phishing messages and webpages into the following collection, and also made a quiz, hoping to deepen users' understanding of phishing attacks and prevent accidents.
